BY JULIE A. PALM
A hacker breaches your computer network, downloading personnel records or customer credit card information and then selling the data to identity thieves.
An employee clicks on a nefarious link in an email, installing ransomware that locks every file until you pay up. A disgruntled former employee takes over your social media accounts, sending out offensive and embarrassing messages. A malicious competitor accesses machinery control software, makes an adjustment and throws your production process into havoc.
Cybercriminals attack from all angles—and manufacturers are at risk.
The 2017 IBM X-Force Threat Intelligence Index shows manufacturing was the third most-attacked sector in 2016 and, more worrying, “in manufacturing, the proportion of ‘security incidents’—those attacks to which we give our most serious classification—was almost 40% higher than the average across all industries.” The statistics come from the 2017 Security Trends in the Manufacturing Industry report from Cambridge, Massachusetts-based IBM Security.
An assessment from NTT, a global cybersecurity provider with U.S. offices in Pittsburgh and Omaha, Nebraska, is even more ominous for manufacturers.
According to NTT Security’s Global Threat Intelligence Center, in the third quarter of 2017, the finance sector was most often threatened by malicious activity (25% of total attacks), but it was followed closely behind in second place by the manufacturing sector (21% of total attacks).
Breaches, thefts, hijackings and other cybersecurity incidents against manufacturers don’t typically make headlines the way those against, say, Equifax or the Democratic National Committee did. That’s because they generally don’t involve such large numbers of victims or victims of such prominence. It’s also because manufacturing, as the IBM report notes, isn’t regulated or publicly scrutinized in the same way as other industries. Depending on the nature of the incident and applicable laws, manufacturers sometimes can choose to keep a security breach quiet. A notable recent exception is the electronic theft of trade secrets from ThyssenKrupp AG that was disclosed by the Frankfurt, Germany-based steel producer in 2016.
So, the threat against manufacturers is real, if not well-publicized.
But, disturbingly, Cisco found that “40% of manufacturing security professionals said they do not have a formal security strategy, nor do they follow standardized information security policy practices such as ISO/IEC 27001 or NIST 800-53,” according to the 2017 Midyear Cybersecurity Report from the San Jose, California-based technology conglomerate.
And criminals seem to know this. “This industry is a tempting target, as many systems within the sector are perceived to be weak by design as a result of a failure to be held to compliance standards,” according to the IBM X-Force report.
Robert Herjavec, founder and chief executive officer of Herjavec Group, an information security provider headquartered in Toronto, is hopeful that manufacturers will invest more in cybersecurity efforts—from staffing to infrastructure.
Herjavec points to the health care sector, which he says has taken note of its own deficiencies, felt “the pain of their antiquated systems” and begun pouring resources into cybersecurity.
“(They) have had to step up out of necessity to do more to protect their infrastructures and patient data,” Herjavec says, adding that he expects more “traditional industries” to do the same in 2018.
“Particularly in the manufacturing space where compromises like CryptoLocker (ransomware) have done some real damage, we will see organizations maturing their security programs and investing in order to keep up with ever-changing exploits,” he says. “Manufacturing will be the new health care in 2018.” Herjavec’s comments are included in a news release for the 2017 Annual Cybercrime Report from Cybersecurity Ventures, a research firm and publisher based in Menlo Park, California, that specializes in the global cyber economy.
Breaking and entering through email
Whether they want to steal information, hold your files hostage or gain competitive advantage through sabotage, cybercriminals have a host of sophisticated tools at their disposal.
“Our adversaries are becoming more and more creative in how they architect their attacks,” says Steve Martino, vice president and chief information security officer for Cisco. “While the majority of organizations took steps to improve security following a breach, businesses across industries are in a constant race against the attackers. Security effectiveness starts with closing the obvious gaps and making security a business priority.”
That said, cybersecurity experts say the past year has brought something of a return to basics among high-tech criminals.
Cisco notes that “spam volumes are significantly increasing, as adversaries turn to other tried-and-true methods, like email, to distribute malware and generate revenue.” In fact, Symantec, a provider of security products headquartered in Mountain View, California, calls “malicious emails” a recent “weapon of choice.”
Symantec points to a recent rise in a particular email scam, the business email compromise, or BEC, in which a fake email ostensibly from the chief executive officer or other senior manager instructs the recipient (a bookkeeper, accountant, controller or even the chief financial officer) to transfer or send money to a bank account or vendor account that looks familiar.
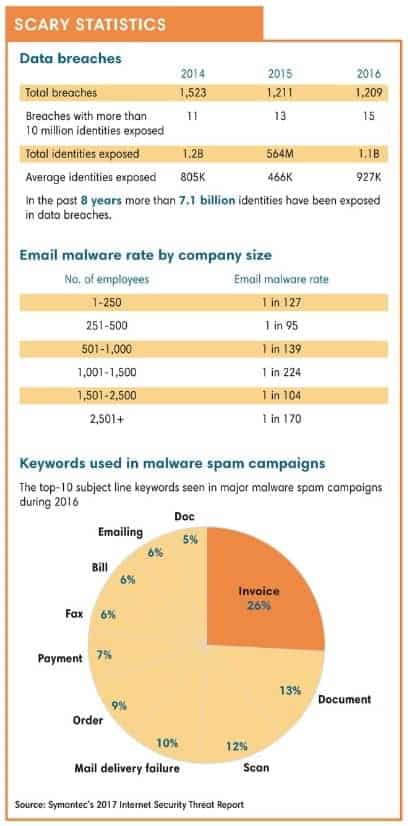
Think of a BEC, also called “whaling,” as a decidedly more sophisticated version of the infamous Nigerian prince rip-off—and one that often works. The FBI estimated in February 2017 that criminals may have stolen as much as $3 billion worldwide using BECs since January 2015—that’s $3 billion in two short years. Symantec estimates 400 businesses are targeted by BEC scams daily.
“A new technique recently observed by our researchers is the ‘hijacking’ of legitimate invoices sent by companies so that the account number is changed to that of the scammer. Some cases we have seen involved scammers attacking the email server to change the details on the invoice. Others were just fake invoice emails sent without the need to hack the email server, but which were effective provided they went out before the legitimate invoices,” according to Symantec. “With BEC scams proving hugely lucrative, they are likely to continue to be a strong trend.”
While criminals have favored entry by email, the number of cyber incidents aimed at websites has been on a decline. “However, web attacks are still a big problem, with an average of more than 229,000 being detected every single day in 2016,” Symantec says.
Companies appear to be doing a better job protecting their sites from intrusion. Although a distressing 76% of websites scanned in 2016 contained vulnerabilities, Symantec found that the percentage of sites with “critical” vulnerabilities dropped to 9%, down from 15% in 2015 and 20% in 2014. And, for their part, hackers seem less invested in their primary means of entry to websites—exploit kits, which Cisco notes are more complicated and harder to maintain than the limited infrastructure needed for email attacks.
Give us the money, we’ll give you your files
With cybercriminals having honed their modus operandi, ransomware attacks—from targeted occurrences to widespread outbreaks like 2017’s WannaCry and NotPetya—should be of serious concern to manufacturers. In a ransomware attack, thieves lock targets out of their files through encryption and demand ransom, typically to be paid in bitcoin. Sometimes the files are unlocked after payment; sometimes not. Criminals can use distributed denial of service, or DDoS, attacks in a similar way, shutting down a website or other part of a business—perhaps the control panel on a critical piece of machinery—and demanding payment.
Symantec says individuals are most at risk, accounting for 69% of the victims of this type of malware infection, but criminals increasingly are targeting businesses through ransomware that infects networks and encrypts multiple computers. Cybersecurity Ventures estimates that a business fell victim to ransomware every 40 seconds in 2017 and predicts that will speed up to every 14 seconds in 2019.
One reason to target businesses: The average ransom amount went from $294 in 2015 to $1,077 in 2016, but when companies are hit and multiple computers on a network infected, the ransom request can be for thousands or even hundreds of thousands of dollars.
Big breaches yield big data hauls
One of the most significant threats to a company is a data breach. We think most often of cases in which criminals steal personal information (credit card numbers, email addresses, birth dates, etc.) and then sell the data to identity thieves. Those breaches are devastating to the employees or customers whose information has been stolen and are damaging to companies in terms of bad public relations and legal liability if a company didn’t take prudent steps to protect the data.
Data breaches also include direct theft of assets—everything from money to trade secrets.
There’s some good news on this front, according to both IBM and Symantec, in that both the number of data breaches and the average cost of a data breach are on a slow decline. But that news is offset by findings that size of the average breach is rising, growing by 1.8% in 2017 to an average of 24,000 records, according to the annual Cost Data Breach Study sponsored by IBM and conducted by the Ponemon Institute, an independent research group specializing in privacy, data protection and information security policy with headquarters in Traverse City, Michigan.
Symantec notes that much of the identity theft damage already has been done, with more than 7 billion online identities stolen in the past eight years, “almost the equivalent of one for every person on the planet.” But that hasn’t stopped hackers from gobbling up more and more data in each breach. “In 2016, more than 1.1 billion identities were stolen in data breaches, almost double the number stolen in 2015, when just over 563 million identities were stolen,” Symantec notes.
Is your machinery secure?
When each step of the production process was discrete and done by a single machine, manufacturers didn’t have to worry about serious cyber incidents on the factory floor. But with manufacturers relying on technology like enterprise resource planning systems and installing complex, computer-controlled and connected equipment, they are at risk of attacks on their very production lines.
Alexander Polyakov lay outs this scenario in a June 1, 2017, blog post for Forbes.com: “Hackers can penetrate the corporate IT network of a manufacturing company, then gain access to a robot’s controller software and, by exploiting a vulnerability remotely, download a tampered configuration file. As a result, instead of a straight line, the robotic arm draws one that is 2 millimeters off. This minuscule defect, if left unnoticed, could lead to catastrophic effects in this hypothetical example—this line is responsible for welding the chassis of a car that, if compromised, could result in casualties and a vehicle recall.”
Such vulnerabilities were, in fact, discovered in an industrial robot, says Polyakov, co-founder and chief technology officer for ERPScan, a business application security provider headquartered in Palo Alto, California.
As manufacturers continue to use automation to cut costs and speed production and as more robotics and internet of things devices are employed, cyberattacks on those devices are expected to increase, too. It’s only natural: Criminals go where the opportunities and vulnerabilities are.
Cybersecurity experts already are seeing attacks on IoT devices, which include everything from refrigerators to security cameras to self-driving cars to machinery—any standalone device that can connect to the internet (and to other devices), typically via wireless connection.
“Most manufacturing systems today were made to be productive—they were not made to be secure,” says Rebecca Taylor, senior vice president for the U.S. National Center for Manufacturing Sciences in an article on ComputerWeekly.com posted in August 2017. “Every manufacturer is at risk—it isn’t a matter of if they will be targeted, it’s a matter of when.”
Top tips for keeping safe

These companies are famous for their products and services—and infamous for being victims of some of the largest cybersecurity data breaches in history.
It isn’t a list any company wants to be on. Cybersecurity experts offer a number of ways to keep your company safe, not only from data breaches but from ransomware (like the worldwide WannaCry attack in late spring 2017) and other threats, as well.
General
- Use “multiple, overlapping and mutually supportive defensive systems,” advises Symantec, a provider of security products headquartered in Mountain View, California. “This should include the deployment of regularly updated firewalls, as well as gateway anti-virus, intrusion detection or protection systems (IPS); website vulnerability with malware protection; and web security gateway solutions throughout the network.”
- Create a formal company policy for employees regarding computer, internet, and email usage and security. Update annually.
- Make sure operating systems and software are up to date on all devices, including desktops, laptops, tablets and smartphones. Updates issued by providers often include security patches for security vulnerabilities.
- Make sure security software, in specific, is up to date to protect against the latest threats.
- Require employees to use strong passwords and to change them regularly. Employees shouldn’t reuse passwords for different accounts and should enable two-factor authentication when available. (It’s offered on most email and social media apps.) In general, passwords should be at least 10 characters long and include a mix of letters, numerals and symbols. Don’t allow employees to share passwords.
- In addition to backing up files and data on the company network, require employees to regularly back up any work-related files and information on their personal devices.
- Ensure sensitive information (confidential employee information like Social Security numbers, company data like bank routing numbers and customer information like credit card numbers) is encrypted while being both transferred and stored.
- Make sure your information technology staff is receiving alerts for new vulnerabilities and potential threats from vendors and making patches as soon as possible. Similarly, make sure IT teams are monitoring intrusion detection tools so breaches are detected quickly.
- If your company uses Wi-Fi, make sure it employs the current WPA2 standard.
- Limit administrative capabilities and administrator-level profiles to reduce the number of employees with access.
- Have a plan in place to manage a data breach, including which employees will respond and what their roles and responsibilities would be. Consult with your attorney regarding potential legal liability and what laws apply if you are the victim of a hack.
- If you are a smaller company without a strong IT team, use a reputable outside company that specializes in cybersecurity to ensure your protection stays up to date and effective.
- Delete suspicious emails, particularly those that contain links or attachments. If you think a link might not be genuine, type the URL directly into a browser to ensure you are going to a legitimate website.
- Be wary of emails—especially those coming from inside your company and those from regular vendors or customers—that ask you to do something outside normal procedures and practices.
- Never reply to a suspicious email. If the email comes from someone you know and you want to double check its authenticity, draft a new email to the supposed sender, pulling the person’s email address from your own address book or your company directory instead of hitting “reply.” Or pick up the phone and call the person.
- “Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content,” Symantec cautions. “Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.”
- To combat business email compromise, or BEC, scams specifically, the FBI advises companies to confirm changes in vendor payment locations and confirm fund transfers using two-factor authentication, meaning verifying the request by phone or requiring a second person to sign off on such actions.
- Report suspicious emails to your IT department.
Mobile devices
- Download apps only from trusted sources.
- Install mobile security apps on smartphones and tablets.
- Frequently back up important data. (Most data plans allow you to back up to the cloud.)
Cloud
- Make sure the cloud services you use regularly back up files and employ up-to-date security measures themselves.
- “Implement smart data governance practices in your business so that you know what business data is being stored on cloud services,” Symantec advises.
Equipment, production systems and internet of things devices
- Train production managers and equipment operators how to identify threats and attacks.
- Implement access control measures to secure against
insecure configurations. You don’t want a cyber intruder to access an entire system from one component. - Change the default credentials on devices, using strong passwords that aren’t shared among devices.
- Modify privacy and security settings on equipment and devices to meet your company’s standards.
- Disable or protect remote access to equipment and devices when not needed.
- When possible, use wired connections instead of wireless.
- Update firmware as equipment vendors recommend.
Sources: Cybersecurity Ventures, ERPScan, FBI, Hitachi Systems Security USA, Symantec Corp., Travelers
Free security tools for small businesses
Cybersecurity is big business. Cybersecurity Ventures, a research firm and publisher that specializes in the global cyber economy based in Menlo Park, California, has estimated spending on cybersecurity products and services will exceed $1 trillion cumulatively from 2017 to 2021.
But free tools that protect against many threats are available to help smaller businesses.
In an Oct. 9, 2017, blog post on Entrepreneur.com, Steve Morgan, founder and chief executive officer of Cybersecurity Ventures, recommends several, including these:
- Avast Free Antivirus (award-winning anti-virus protection)
- Ransim (ransomware simulator that shows a network’s vulnerability to attacks)
- Weak Password Finder (susses out weak employee passwords)
- SiteCheck (scans for “malware, website blacklisting, spam injections and website defacements”)
- ZoneAlarm Free Firewall (“manages and monitors all incoming and outgoing traffic and shields users from hackers, malware and other online threats”)
- ProtonMail (“free secure end-to-end encrypted email accounts
Insure yourself against threats
You’ve taken prudent steps to protect your company from cybercrime. Can you bear the expense if those precautions fail?
Traditional business insurance policies typically don’t cover cybercrime. In fact, CyberPolicy, which advises companies on purchasing coverage, estimates only 3% of small businesses carry such insurance.
A comprehensive policy should cover both your direct costs (including customer notification and credit monitoring, legal and PR services, recovery and restoration of corrupted and destroyed data, and reimbursement of lost income during the event), as well as third-party costs (litigation and settlement expenses related to losses customers and vendors suffer if you unintentionally fail to protect their sensitive information). Separate crime policies, which traditionally cover financial losses from robbery, burglary and forgery, often now cover the cybertheft of money through phishing and other means.
Check with your insurance agent or a broker who is well-versed in cyber insurance policies to make sure your coverage is comprehensive and addresses the latest threats to your company.